We provide a new service for protection from DDoS-attacks. It is designed for users of "dedicated server" and "Placing a server," as well as for customers who rent server rack.
To learn how to be protected, we describe in detail in this article.
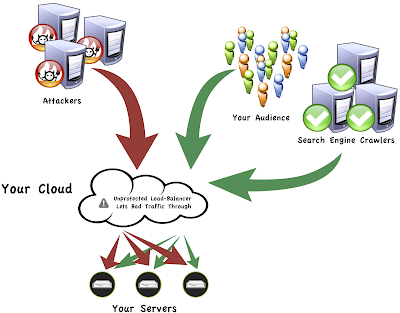
DDoS Attacks: A brief overview
Abbreviation is DDoS Distributed Denial of Service - attack distributed denial of service. DDoS-attacks called malfunction attacked machines by sending requests to it from multiple hosts.
Typically, DDoS-attacks are carried out through a botnet - a network of computers that have installed malicious software (called zombification).
Some types of attacks can be carried out without a botnet (e.g., UDP-flood).
By all objective DDoS Attacks can be divided into the following groups:
The attacks that aim to overload the bandwidth. Examples of this type of attack can serve as mentioned above UDP-flood, ICMP-flood (aka ping flood), and other practices of sending packets that are not requested. The strength of such an attack is measured in gigabits per second. It is constantly growing and now can be up to 100 or more gigabits per second.
Attacks on the protocol level. As the name implies, this type of attack using the vulnerability and limitations of various network protocols. They "bombard" the server parasitic package and it becomes unable to process legitimate user requests. As an example, SYN-flood, teardrop and other attacks that disrupt the normal movement inside a package at various stages of the protocol.
The attacks on the application layer disrupt the normal functioning of the system using a vulnerability and weaknesses of applications and operating systems.
For more information on the issues of classification of DDoS-attacks, we shall not stop - the interested reader can easily find the Internet a variety of materials on the subject. Much more interesting to us are the existing methods of protection against DDoS. They will be discussed below.
Methods of protection against DDoS
Methods of protection from DDoS-attacks are divided into two large groups: methods of prevention and response methods.
To prevent DDoS-attacks are commonly used hardware methods of perimeter security - firewall combined with intrusion detection system (Intrusion Detection Systems, IDS). However, protection in a strict sense they do not provide.
DDoS-attack is quite possible to organize and within the permitted firewall packages. Regarding IDS, they typically operate within the signature and the statistical analysis, comparing the incoming packets with the existing traffic patterns. If the attack is carried out by conventional distribution network packets that individually are not malicious, not all IDS can detect it.
In addition, and firewalls, and IDS devices are often controlled by the sessions, so can themselves become the object of attack.
An effective means of minimizing downtime when DDoS-attacks are multiple reservation - Organization of clusters of servers placed in different data centers and connected to different communication channels. If one of the components of such a system will fail, clients will be redirected to the server is running. This method has only one drawback: the construction of a distributed cluster with multiple redundancy requires a very large financial costs.
The methods used to respond in situations where an attack has already begun and it must be stopped (or at least minimize its consequences).
If the purpose of the attack is a single machine, you can simply change its IP-address. The new address is then possible to give only the most reliable external users. This solution is hardly ideal, but it is quite effective.
In some cases, help filtering techniques. After analyzing malicious traffic can be found in him a certain signature. Based on the results of the analysis can build a router ACL or firewall rules.
In addition, most of the attacking traffic often comes from a particular provider or backbone router. In this situation, a possible solution is to lock the direction from which traffic enters a questionable (it should, however, bear in mind that legitimate traffic in this case will also be blocked).